Home > Run and Grow > Risk Management >
5 Business Risks in a Hyper-Connected World
By: SmallBizClub

In today’s hyper-connected world, the old boundaries between companies and the outside world are only fading. Efficient communication systems, and innovations spawned by the internet and mobile devices, have enabled companies to connect, reach, and spread ideas. It has helped companies to maximize efficiency, increase sales, and reduce expenses.
Yet, evolving technologies such as cloud computing and big data are exposing businesses to larger risks such as cyber theft, fraud, and sabotage. The weak links of information systems are vulnerable to attacks from cyber criminals, competitors, and even employees.
Protecting Business Assets
Businesses have to look at risks, access the capabilities and install security to prevent attacks or infiltrations. Despite all the good intentions and knowledge of security issues, most businesses are lax with risk management.
A report by McKinsey & Co on “Risk and Responsibility in a Hyper-connected World: Implications for Enterprises” showed how most executives put dangerous threats on low priority and weren’t ready to make the necessary changes.
Companies serious about risk management should deploy active defences to thwart any kind of risk or threat. One way to integrate enterprise-wide risk management is to learn, incorporate, and prioritize actions. In order to achieve overall efficiency, it’s important to automate certain functions, so that human intervention can be used for key tasks.
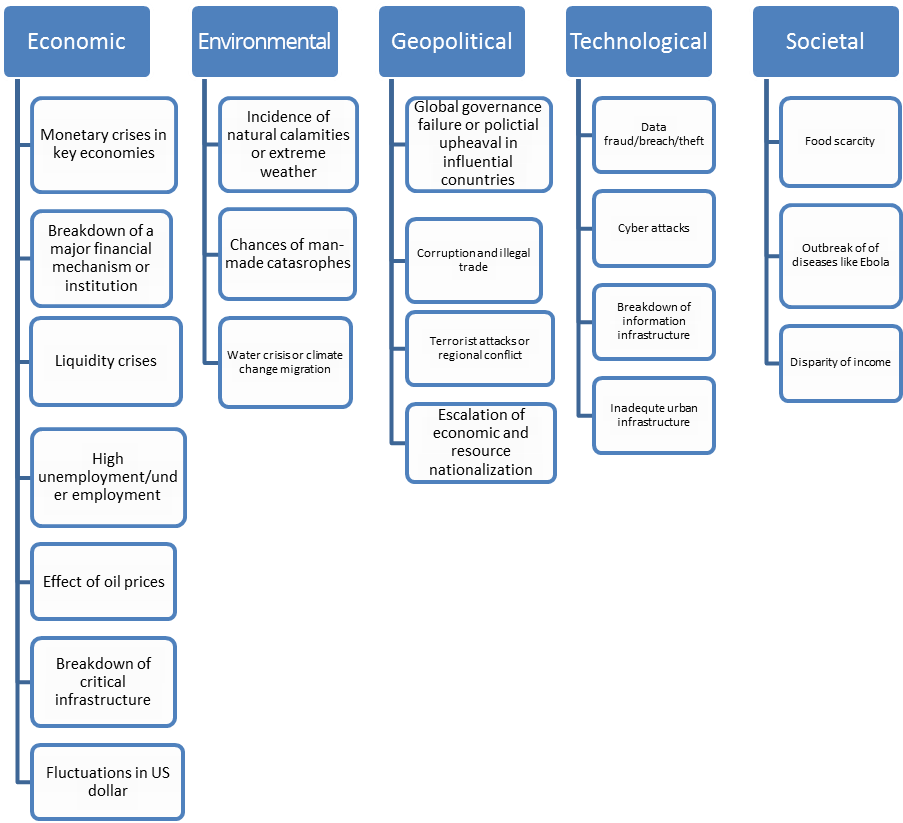
Global Risks 2014, an insight report published by the World Economic Forum, has identified 31 global risks in five categories: economic, environmental, geopolitical, technological, societal.
Related Article: Minimizing Small Business Risks: What Every Owner Can Do
This report looks at the overall global perspective of risks. Nevertheless, it has lessons for senior executives and business stakeholders to understand how global risks are evolving and businesses are getting exposed to certain global vulnerabilities due to worldwide connectivity.
Recall the risk categories. Here are the risks likely to hit any business operating in a connected environment.

Economic Risks
Risks in the economic category include stock market swells and crashes, failure of any financial institution, labor unrest, breakdown of law and order, general unrest in any region or the collapse of markets in a country. Companies operating in unstable economies should keep a constant eye on the economic health of their environment.
Environmental Risks
Risks can ensue from natural disasters like flood, drought or super-storms, earthquakes, or man-made reasons like accidents in industry, shortage of water, etc. Companies located in regions prone to earthquakes, floods or cyclones should consider the possibility of disasters emanating from natural sources.
Geopolitical Risks
Companies operating in regions prone to political turbulences such as corruption, diplomatic problems, high crime, disputes, strife, illicit trade, or labor unrest must consider the possibility of hurdles in taking their plans forward.
Societal Risks
Problems related to social instability, income disparity, food crisis, outbreak of pandemics, breakdown of land order, etc. can disrupt internal and external operations of a company.
Technological Risks
In this hyper-connected world, there’s always a threat due to centralization of information and communication. Being over-dependent on the central networking unit or a cloud-based system makes every organization vulnerable to security breaches, data pilferage, cyber-attacks and more.
End note:
In the face of high stakes, senior business leaders should address the challenges and loopholes of current risk exposure for their organizations. For improving organizational risk competencies, it is important for business to:
- Take stock of the existing capabilities and risks
- Provide a clear approach and controls required to protect attacks
- Create a scalable organizational risk management model
- Install a tolerance limit and metrics
- Create the right responses during any breach
Author: Mohammed Nasser Barakat is the Consultancy Director at CAREweb Corporate Governance Consultancy, offering Governance, Risk & Compliance (GRC) software used by global business organizations. Nasser is a Certified Control and Risk Self Assessment Practitioner (CCSA) and has 8 years’ experience in internal audit solutions, Business Risk Management solutions and consultancy.
Published: January 12, 2015
6737 Views
6737 Views












